Exploring cyber security through a Capture the Flag (CTF) game
Nulab Staff
December 04, 2023
As a developer, ensuring the security of your applications is crucial to prevent unauthorized access and potential cyber threats. Unfortunately, many young developers don’t have much experience or interest in security issues until they start facing incidents. After working through the stress and repercussions of a few patches, security quickly starts to play a much bigger consideration in the seasoned developer’s mind. Luckily, there are easier ways to cut your teeth. In this article, we’ll explore a gamified approach to learning about information security – Capture the Flag (CTF).
What is Capture the Flag (CTF)?
Capture the Flag is an engaging and interactive information security competition that allows developers to enhance their skills without putting their actual products at risk. It’s a game that offers a practical and hands-on way to learn about various security challenges.
Capture the flag rules
While specific rules may vary between events, the fundamental principles include:
- Point System:
- Teams accumulate points by successfully solving challenges.
- More complex tasks often yield higher points.
- Sequential Task Resolution:
- Teams must solve tasks sequentially.
- The next task unlocks only after successfully completing the previous one.
- Time Constraints:
- CTFs typically have a set time limit.
- Teams strive to accumulate the highest points within this timeframe.
Types of CTF challenges
The three most popular types of challenges are jeopardy, attack-defense, and mixed.
Jeopardy
Jeopardy-style CTFs present a diverse range of tasks covering web security, forensics, cryptography, and more. Teams earn points for solving challenges, with complexity determining the points awarded. Tasks must be solved sequentially, and the team with the highest points at the end emerges victorious. An excellent example is the Defcon CTF Qualifier.
Attack-defense
In Attack-Defense CTFs, teams defend their own services while attempting to hack others. Each team manages its network with vulnerabilities, earning points for successful defenses and attacks. The team with the most points at the end wins. The DEF CON CTF is a prime example of this format.
Mixed
Mixed competitions blend elements from different formats. For instance, an Attack-Defense game may include task-based challenges. The UCSB iCTF is a noteworthy example of a mixed competition.
More types of CTF games
While jeopardy, attack-defense, and mixed challenges form the core, CTF competitions feature a plethora of specialized challenges:
- Reverse Engineering (RE): Dive into the world of reverse engineering, where participants unravel the secrets of compiled programs to find specific inputs or extract hidden information.
- Binary Exploitation (Pwn): Explore vulnerabilities in binary programs, crafting inputs to seize control of a program’s execution and demonstrating prowess in exploitation.
- Forensics: Analyze files, logs, or network traffic to extract concealed information or uncover security incidents, showcasing investigative skills.
- Steganography (Stego): Decode hidden messages within seemingly innocuous files like images or audio, revealing the art of concealing information in plain sight.
- Web Exploitation (Web): Uncover and exploit vulnerabilities in web applications, whether it’s SQL injection, cross-site scripting (XSS), or cross-site request forgery (CSRF).
- Cryptography (Crypto): Tackle cryptographic puzzles or algorithms, decrypting codes to unveil concealed information and showcasing cryptographic expertise.
- Networking: Analyze network packets, identify vulnerabilities, and perform tasks related to network security, demonstrating a solid understanding of network protocols.
- Mobile Security: Focus on the security of mobile applications, exploring vulnerabilities unique to mobile platforms and enhancing mobile security skills.
- Hardware Hacking: Engage in challenges related to the security of physical devices, embedded systems, or hardware components, showcasing expertise in hardware security.
- Specialized Challenges: Encounter unique challenges that defy standard categories, requiring creative problem-solving skills and pushing the boundaries of cybersecurity knowledge.
The diverse array of CTF challenges ensures participants develop a well-rounded skill set, fostering expertise in various facets of information security. Whether unraveling the intricacies of reverse engineering or tackling cryptographic puzzles, each challenge provides an opportunity for skill development and creative problem-solving.
Best practices for excelling in CTF competitions
Participating in CTF competitions can be both exhilarating and challenging. To maximize your success, consider the following best practices:
- Diversify your skills.
- Develop proficiency in a variety of cybersecurity domains, including web exploitation, reverse engineering, cryptography, and forensics.
- Stay updated on the latest security trends and emerging technologies to adapt to evolving challenges.
- Build a strong foundation.
- Acquire a solid understanding of networking protocols, operating systems, and programming languages, as these form the basis of many CTF challenges.
- Hone your problem-solving skills to approach challenges systematically.
- Collaborate and learn.
- Join online communities, forums, or local CTF groups to share knowledge and learn from experienced participants.
- Engage in collaborative efforts during CTF events, as teamwork often enhances overall performance.
- Practice regularly.
- Utilize platforms like Hack The Box, OverTheWire, or other CTF platforms to practice various challenges and sharpen your skills.
- Set aside dedicated time for consistent practice, focusing on areas where you feel less confident.
- Document your progress:
- Keep detailed notes on the strategies and solutions you employ during challenges.
- Document new techniques, tools, or concepts you encounter, creating a valuable reference for future competitions.
- Embrace a creative mindset:
- Approach challenges with creativity and an open mind, as unconventional solutions are often required.
- Think outside the box and consider alternative methods when faced with obstacles.
- Stay calm under pressure:
- CTFs are time-sensitive, and maintaining composure during time constraints is crucial.
- Practice time management to allocate appropriate time to each challenge and avoid getting overwhelmed.
- Explore tools and resources:
- Familiarize yourself with commonly used cybersecurity tools and resources.
- Experiment with different tools to find the ones that align with your preferences and enhance your efficiency.
- Learn from mistakes:
- Understand that challenges may be difficult, and failures are part of the learning process.
- Analyze mistakes, understand the root causes, and use them as opportunities for improvement.
- Contribute to the community:
- Share your knowledge and experiences with the cybersecurity community.
- Contribute write-ups for challenges you’ve successfully completed, helping others learn and fostering a collaborative environment.
By incorporating these best practices into your CTF journey, you’ll not only enhance your skills but also contribute to the vibrant and supportive community of cybersecurity enthusiasts.
Nulab’s CTF game
At Nulab, we created our own CTF challenge called NU CTF for our developers. The challenge consisted of three categories: Reversing, Crypto, and Web. Each category had challenges with varying difficulty levels and point values.
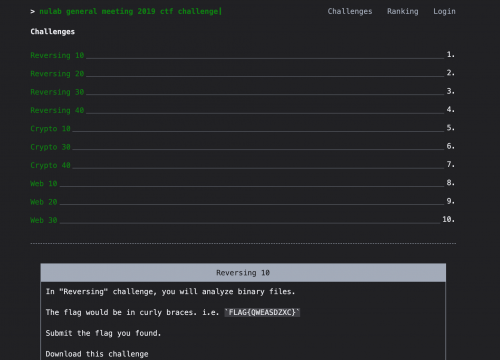
Developing the portal itself for the challenge provided us with an opportunity for our team to explore new technologies like Vue.js and Golang. We also used:
- Vue.js
- Golang
- Fabric
- Ansible
- AWS
- C
- Python
Results and takeaways
We had over 7 contestants participate in our CTF challenge, and some of them successfully solved all the challenges. This experience demonstrated that CTFs can be an effective and enjoyable way to make web security more familiar to developers. It not only enhanced our security knowledge but also fostered team bonding.





Try NU CTF yourself!
If you’d like to give one of our challenges a try, here’s one from NU CTF:
Find the text “FLAG{dyi8763R}” to complete the challenge.
H4sIACyzlFwAA+2dDZyNZf7/r52Uh5CnkKTZkgpxZpyZ0SRJpKyENMmWjCR5SgzNz0qSl5WdNEmt eqm1ZdX0stYiCYlWkpWYlbWyspKQp5QhqfM/n6vu+d/nOtc5c+6nc86Yz/v1up0597nPdV3nfnJ/ ru9T3vCRrYXH+Hy+rIyMVPma+fOrL93/8+svpKa18fsz0tqk+TP8qb609LSsNJGa4fXAwJjRebmj gkMZOmbE6Lwo2wU3GzQoyue//I7S13JCXvD45+fmetpHcH9k+v0Rjn96elZWepp6/LN8PpHq83RU v1DBj/9TPbp3qVGtUbXgnzVuvaVTLyHO2R/8u0+V84L/Dnriv9WFSBW3drqxd/6vRFFBzuhfBYIk eMyEEEIIIYQQQkiFJyXRAyCEEEIIIYQQQki5FejtNs/caPgCJHoshBBCCCGEEEKIu5RTsU4IIYQQ QgghhJxdUKAngDvXTM2hLwAhhBBCCCGEkEhQrBNCCCGEEEIIIUlApUQPgJQ3rq9SeJi+AISQ8s/R o0dFSUmJSElJERdddFGih0MIIYQQEgJLsZFyweLFi8Xq1avFjh075MN1u3btxKhRo8QFF1yQ6KER QsoRnTt3FitXrpR/N2rUSPTr10+MGzdO1KhRI8EjI4QQQgihQCdJzo8//ihGjBghXnjhhbDP6tSp IwoKCkRubm7M7Z2347U59AUghIDf/OY3YunSpSHrmjRpIubPny8yMjISNCpCCCGEkF8oKsgZTcVO kpaTJ0+Krl27SlN6JBo2bCi++uqr+A2KEFKuee2116QZXaVKlSpixowZ4oEHHkjAqAghhBBCfoYC nSQt9913n3j11VfL3O706dPi3HPPjcOIEsiKb5Y/Rl8AQlzlhx9+ED169AgzqxssWrRI3HbbbXEe FSGEEELIzzDdO0lK/vrXv0YU6sj81LRpU3HeeeeJDh06nP1CnRDiGrhfvPXWW2Ljxo0yfgb3EjNI fPH9998naHSEEEIIqejQmp4APvnkE7F7926RnZ0tGjRokOjhJB0nTpwQzZo1E/v27Qv7zO/3i1mz Zok2bdrI4PUzZ86IypUrJ2CUxAJ/eyT7dfoCkKTn66+/Fi1bthQHDx4sXVdYWCgefvjhBI6KEEII IRUVWtPjDOKohw0bJnr16iUaN24s7r77bvH5558nelhJxcyZM8OEOizo+fn54p///KcU6uCcc86h UCeEOOLCCy8Us2fPDlk3Z86cxAyGEEIIIRUe29Z0JPZCbaxt27aJ7du3i507d0oLMawQ3333nbRy 1qxZU9SqVUsuxt/qKxYkAEtNTRUXX3yx278v6ejSpYtYvnx5yLrq1atL1+6ePXsmaFTJAyzkSLes CnS4oD799NMJGhVxCjwkTp06JSpVqlT+auh90fqi0fQFqFCoeTHw/9zVV1+dwBERQgghpCJiS6y/ /PLLYtCgQeKnn35ydTCINYZQQ6xgx44dxcCBA0Xt2rVd7SORPP/889KSrgMiZvPmzaJFixaejwMT LUuWLJHJk7Zu3SqOHTsmhRQSstWvX19a+XEcMjMzZab1iy66yPMxGSBmtFu3biHrMBZMCFWtWjVu 4yDO+ctf/iKtkuvXr5cTeAbVqlUTrVq1EiNHjhS9e/eWXhFugUkBTBoeP35cntOYNIQnBhZcY+a/ sdSrV09OFiZDfgOMvbi4WE5gxkMYfvnll2LhwoXyvrN//35x5MgRWe8Q+8Pn84k+ffqIunXrej6O ZOFf//qXPC8Npk2bJsaMGZPAERFCCCGkImJLoA8dOlRbzNpt8PAMEXk2FLH9z3/+I9LT00VJSUnE bSBMFy9e7Ok4nnvuOTF58uSQ2MtoQMy0a9dOTpbce++9no4NPPTQQzL23AysWvHom7jDN998I7Nn RyuhZ4BJIIh4NwTpH//4R5GXlxf1GosEhOlll10mx4MyXVlZWY7HY4VnnnlGTJo0SU6WAYzhlVde cWPy4n/dbj0a0RfgwIEDMoxk7ty5cjIjEpg8zcnJkWP89a9/7XRMISBRGyYmsOzatUsuhw4dkhMG 5okdHB/EjWPp1KmT595XmBw2jkffvn3lhBMhhBBCSFwJ2KB///4Q+HFZevfubWeISUfbtm1j+r3v v/++J/0HH34DHTp0cHQsWrVqFdi8ebMn4zO46qqrQvps0qRJICgiPO2TuEdQXMV8rhtLtWrVAhs2 bHDUb1DgBYKC0rX7zogRI1zaI2UzZMgQ7RiCAtr1vrZt2xaoX7++pX1RvXr1wNKlSx33jWM8ceJE eX7YPVY+n0+2sW/fPhf2RjjNmjUr7at9+/ae9EEIIYQQEg1RVJAz2lYGOQSTxwsEvkfjzjvvFK1b txYvvvhi0tbQ+fOf/yz9fmMB5m63gY87zPWxmDijAZNX8MlVvPfee+4MTAHHTz3eMOW76RPthLff fluabY8ePZrooSQtQXUb87luABM4zLXffvut7X7Xrl0rYzbcAi5D8An3mqeeeiqiexISgLgN4gxi dacxgFkb/u9wC7LKF198IR5//HFx+eWXS3eFoMKW50csxyrzh0ezo+UFgK8+2sP/R/BNR8yAW6Co OmInDBA/QQghhBASb2z5v+OhCA99CxYskD6KkUDGOKTRRcAlHnbgS4jA0Uive/fulYs58L158+bi 008/jdgHgqcRXAmQQh1Ft5OJaHXG4A8PkQL/UzNuZy666667xJtvvulae1dddZX497//7Vp7Bkh7 Dx9XM8mSxQlZ7jC2PXv2SHGAjIBXXHFFooeVVLz77rvSL9kuEyZMEE888YSt70JI4l7hZtIMTG7d cMMNrrWngnsVrv9IY37//ffF9ddf72qfyOSHe60dMFG3Zs0aG9/MGz6ydX7uAFu9xorP58v0+1Px mpWZIV996T+/D/6RnpWVnpaa1sbvz0hrk+bP8Kf60tKzfGki1efpqH5hzOi83FHBoQwdM2J0XpTt gpsNGhTlc/ljfKmlr2cLH3/8scwHgEeKaGEYTsF/XejDjf9StmzZIvM4GODWt2LFCsftEkIIIYRY wqkLx969ewP79+8PdOzYMcyd9Z577rHc3qlTp6Qb78KFCwPTp08PrF27Nuq25v4qVaoUCGoVJz/H dcaPH6919cVYEW5QUlISqFOnTshngwYNcq3/2bNnl+l2DHfloK4MvPTSS4Fly5YFlixZIv8eO3Zs IPiQKseqfgfH3G02btwY0kfjxo1d78MuQREQMrYJEyYkekhJB1zKdefXLbfcEli5cqV0kZ8/f36g V69e2u0aNWrkqP9Jkya5FiaBaxLXplds3749ULNmzYj9DxgwwJN+09PTw/rCOLp27SqvdXOIgG5Z t25d1PYRqoKwNjeOgZVj5TTEBsyZM8fF+/DDW88/YLiOOB4aIYQQQioojsU6gGhGzKv6EAXB7SW7 d+8O6xMPwckCJjKqVKmifcCEiDcYNWpUyGe1atWS+9QpBw8elG1Fe9Dt06eP3I/R2LFjR5iwwISK 2+CB29xHMuWygOBM1rFZ5ciRI663iYkn3fnVvHlzbT6Kvn37arffuXOno3HgtyH2HpMD69evDxQX F8uxbdq0SZ5fWIcJQOQNwaRUJHGKa9IrMAmA/RLpmsQkmVfgdzdt2rT0PoMJDnVSAveDbt26lXnf 0jFlyhRbghv3F+RbwX6fN2+ePE64l2/dulUeLwhp5JhQ850YC46j03vmyJEjQ9osLCx01B4hhBBC iB1cEeh4INY9cLkhMqOBhzi1XzesKm6hPvCZRcvp06dLt4OI8GJyI1IiMyzZ2dly/8VKQUFBiFX9 2LFjjsenolrTyxID8SQ1NTVkbPn5+YkekiUgfJEoFNcljmO/fv3KnJixApLA6c4ziGAdkQR9NO8Z t4EwRbJDdQwpKSmOJwqiEem6xHGBN4vX4N4Dq3c0bwFc3w0bNgwbI7xuohHpPNAt8JZ544035ASg FeAhpHogYZk2bZqldlRUj7B4HItkpXHKw7+iLwAhhBCSeGzlHVRB3XYV5LmrXLmyG81HRJdGAXXi kwHkpkMaBx2FhYUhtb2vueaakJhI4DT1wOHDh2UpMB1BsSA++OADS+XKRo8eLdMxYFwI40dItNuo MayNGjVyvQ+7GOkyAGq0Dx48OIGjsQbyXqKGOErmIYwd+xnlEd38DevWrQtbh/J4t9xyi3b7SNep nTJ8dlm1apW2v5tvvlnmyfMCpHtQS1UaoAxhly5dPOnXDO49KMdXtWrViNvg+kZqGJWyjg/S18QK 8h8iF6HVlCD333+/THGCc9oM7qvIF2gX5DE007BhQ9ttEUIIIYTYxRWBDsGmAoHuNUYdZAPUg0bu wWQAyb7NdaIN8PDfuXPnsPW9e4fmvl65cqWj/jE5oEtm3aFDBzFjxgxbbV544YWyEINu/G6g5lxD jspkALXjzfuyY8eO4tJLL03giGIDhRaGDh0q+vfvrxVWuG4xkeMG6rUIkHwrUlGHSAU/UlJcuSXF hG5iEQyKmu7NPijQgUIXutyCyJOIJPfJhJ1CC7i/4T5sxpjQUv+fQPuRjkFZNGjQQLzxxhsh5wsm EHX/F8UCJlTVCd/69evbaoskmv+9O+S2aCUlCCGEkPKD4ydjVN7atWtXyDo8nEWyormJKoaTxfoB kaQTxHiwRPZjHd27dw95D0tTtIIIZaGzxlevXl1aVJOlKp6KlxmhnaAWdWjatGmCRhI7RtbqSBXi 3KZKlSoxrTPYvn27dn08r+GlS5eGrcMEUdeuXT3pb+rUqSGV4Qxwv4Tni9feR1ZBkRaVaMcUtGjR QmzcuFFOPAwYMEBWJcXEDKpf6iYpyqrSGg1kd4fHhhkUU7CDbpIoWSYLCSGEEFKxqOS0AbgIqg9e 2dnZonbt2k6bLhPVQpgs1o9FixZpS1nfc889onXr1trvwOUdLsDmh2I8bOKB1yr/+9//xKZNm8LW T5o0KamtwKoQdrNsuhPMru4gWSaCIoFJM3iz6ASWASyew4YNE3Xr1nWlz3r16oWtU92HzaDUugqE arzCVf71r3/JKowqPXr08EQo45osKCgIWw9hCHFuJfQkHqBSpS6EIZZzH/cyLCq66qXVqlWzN8Ag H330kTh06FDIukgTP2Whm3iIFg5AiFe0yHnvHfoCEEIIKaWoIGe0Y5O6Thl6ZZJSUf27k8UEguBf FTyZ5+fnR/0efNPN6J6YY2HhwoVh66CEEJiezKiuGfH0hY6GqjSSZWYoEghCj6TWodTHjx8vP3/6 6add61OXTKC4uFiqKpUDBw6I+fPnh62H77QXiQ90RPK77tu3ryf9wcSsi0FAUPq9997rSZ9OwD0E 55GKkxkV3TnZsmVL2+2NGjUqbJ1dtxx1lqYs1wFCCCGEEK9wrIB0ZjNVaHpFMgr0r7/+Wixbtixs PWIA4KMZjfbt24e8d1Ogjxw5Mul8alV0/sDJQHkzqWN8umsBPvDwR37yySdlsgE3QdC+DgTHI/jX AKZsbKuaQgFcTuKFzt8dEy+RfocT/vvf/4q5c+eGrYe/9rhx41zvzynIwjZhwgTtZ7qscrGiM6kj MN8ORUVF2vsj4nrsYg6sd2LqJ6RCUnfGyyX0BSCEENdxLNZ37NgR8h5WiPT0dKfNxoTqH+3kQc0t kOFIZ9GB1aws2rVrF/Ie1mWIfyvgQVv1LcZDaL9+/Sy1kwhUz4xktaYnu1hHAgKz8IVfOc6/DRs2 aP2S3aBnz55hJQsA/JER0H/77beLjIwMmaIbqbpVIJThex4PMHmg879HzIAXyRumTJmivSfAqyFe 3gNWQMY73THCJKzV1OxmdGK9WbNmltv5/PPPZeyGjrZt21puz8BsQac1nRBCCCGJwrECUjMA+f3+ kFpjXqJa05PBAqLL3AbhcuONN5b5XVjb1UBfqxZ1iDB1v8BK77b11G0gmlSBnixu5ao1PVnGFY3n nntOnotIXQ6R/Ic//MHz6xJZE3WTKkijjaQNsORHAqEg8QoIXrt2rVYwe5H1EhNs8+bNC1vfpEmT pAs/OXHihMjNzY0YrjN9+nRH7asCHd4E559/vqU2UHoBEyk6bwxMRKllM6xg/v8jnnUBCSEJ58dH m11IXwBCSFLiSKwja5WaNQ2Z5OKFKkoTbQHBg6TOSoe0x7Gi7j9de9GAEFFBzG+ys3r16rCshF6n VV+xYoV45JFHxHXXXSeLSV9yySXS2ozac6hphqLjOMetur6/+OKLIi0tTTz++OOOijkbYAyI57YK 6uhhLF4VAle5/vrrtfHCZYEabjgO8UKXEhxCz4vrJFKNxBEjRiRNKArKU7z88svSDR3lIHTguOKc doIq1lNTUy19H5MJcL3XWfpBTk6OvIbtYi78jrh8ZNQjhBBCCIk7AQds2rQpgCbMyxtvvOGkSUv0 69cvpO/x48fHrW8d8+fPD9sfwQf/wMGDB2NuY+rUqSHfb9++vaUxdO/ePWwMOE7JzoABA8L225kz Zzzpa9myZYGWLVuG7SfdUqVKlUC1atVK3wcf4stsf+zYsaXbDxs2zNFYS0pKAg0bNpRtDRw4UL5P ZnDMOnbsGNO+xTEOCtVAUMDGdYx+vz9sLO3atfOkryZNmmjPqSNHjnjSnxU2bNgQGDRoUKBWrVpR jxP21+nTpx31hfMCx9vcLu5VsbJ///5Aenp6xDHiuty7d6+jMXbq1CmkzUOHDjlqjxBC4kLR/Kee N3wBEj0WQojrOLKm6wrfXnbZZU6atITqnphoa7ougRwsdFbcztX4dLiyw9oVK2oyNrhpO7WCeQ28 EBDTbwYZoN2OE4Z7/R133CFdnLdu3RrTd2AJNZ9nsbi9m5ORzZo1S3z22WfWB/sLsMYa1nz8Dfdy q8Ci/uCDD4o1a9bYHkesIFeFrvqDCs5zuOQ/++yzcbUqwzNBl/zSC0s69reu/hv6ikftymgguR1C Yl566SVx7NixiNsh3wdc952GTeAcVsMNdNUBdHz88ccy5jzaeYX6dhdffLGjMao5VdS8K4QQQggh 8cBR8XSdQPfaRdmMWioo0bHpy5cvD1tntbRTZmam/B2GKIRARHx6LLHtQHXN1oUfQPAjTAHxncZi JOIzYovxiodzuICaF8TOuy2ckQVbnWxxO04YggQlAp0+dOuKhKtA+GCyCMcOomTq1KnSndgqOE7T pk0LWYcs/o8++mjMbSA2Gq7K2L8QY5MnTxa/+93vLI8lFjDR0r1796iCzwAiGeI1Xq74BriWdHHp XoTpqJNOBrjeunTpIkNZvvvuO3mtGdcXkqkhnwAmkryksLBQ64ZvBucwrk0nCeMMdInjyhLoCBVB 4j2cs9FKrCF0wI39hfuD+XpbsGCBuPbaax23SwghJCJ3HfuxPvMCEBIFV8U6EgNFsxIdPnxYJpXC AyqEtvGgiodCLBCHeFiN1bqmioJEZnr/4osvwixniHe1WkMeViuIPbNlHnHbsYp1NcGSri4xJlQi 1dUuCxwvlPyCVRkLvCeQBOzKK6+01d6nn34qCgoKwta7KdajlQKzSiwTQkiIBospkqcBWCPxG61a UCGu1eOERI1W2zBPhGAcOF5eZDTHxJRuAk8Hrn1ko4doj2eSQ11cOs5pTJK5DcSeDjU5JHIy4L6I Bd4wmPRDQjQIZa88DcwlyCIB67LV+1ckrIr1t956S5asKy4ujtoujpvu/mGHG264Qd4bjXN45syZ sqxgixYtXGmfEEIIISQmigpyRjsKUEfwtDAF9AVVW2DatGkyQBfB40GlFfD5fIHg01hYcGKkJfj0 KINFg8q0zP6DT1Qh3w2qISc/xxG64PS2bdvaagv70NxOrEHqCIRXx6AmDECgZyzHwcqCY4vAeisg QHfixIkyWFdtDwHZTgNiDRBkmpqaGnX8ON8w/qA6Cmzfvj2wY8eOwNKlSwNBlSA/M2/brVu3mPp9 9dVXQ74XVBKWxo1AdFw35jYQSGwl2QFAgLz6e4OKyVIbsfDCCy/YOncQdB9PsrOzw8bQqlUr1/tB 8LfT6wrn3rFjx1wfG9i8eXMgJSWlzDFMmTLFlf505weuMRVcg7hvxrJ/cH3s3r3blfEZDB48OKwP XMuEEEKImf+W7BrDvAAkHtgS68ePH5cisE6dOq4LP2NBBq+ysvmoWZB0D3/xIj8/P+w3TJo0yVZb apY+CNpYsojt3LkzbAxbt24N2QZi1IvjhXMhVpBZShWi5gUi3i06dOgQsR8I7+Li4qjfh3A3fycn JyemfnGNmLPQYWLJCpMnTw4b78yZMy21AZAtzNwGsui5DSYQIt0L8LtHjhwpBbHucwjGjRs3uj4m Hchah8lAdQzYR26jO352lt69vXsGWLVqVeDmm2/WTpgZS/Xq1V3JqoZMn2rbmDAAmJjD/yfqxFi0 BRPBVieuygLCX50ANpY333zT1b4IIYQQQiJhKYMcgmwRWIkg3T59+kgfTa+An+7KlSujbqP6vMcS POwVyPSmYtdvGxnfED9ggEBSZA778MMPZRBwJNR6ZkDN6IdaYl5k2sO5cPLkyZi2RbyDzgcWYGyD Bw92ZUyop4Z4AV0fyMa2ePFiWX8tGqqfvLlmUzRq1Kgh60MZwI/2b3/7W0zfRVC5GpgO/2PUiLOK GoSM4Ge3mTRpkvZeEBTlMuvXM888I7Zs2aLN0oZzFgH88QD+9UYiBjNW4whiQXc/sMP8+fNFUVGR K22pII7mnXfekffRoADVxgwhNuGFF15w3Jdat9NoG8kSUEge/5/oakmqII4I18bbb7/teqzE2LFj I8ZsWK2LSQghJJ7kDR/ZOj/3AU/78Pl8mX5/Kl6zMjPkqy/95/c+X1p6WlpWRmpaG78/I61Nmj/D nxpcl+XziVSfp6P6hTGj83JHBYcydMyI0XlRtgtuFvVBUP4YX2rpKyHEOeOXN3iWiTgIcYij0heE EEIIIYQQQghxBwp0QgghhBBCCDHY/fe/fUlfAJIEUKwTQgghhBBCCCFJwK8eHD5rBlU6IYQQQggh hJR72j95tCN9Ac4mKNYJIYQQQgghhJAkgAKdEEIIIYQQQkhC+f0nwwfQFyAUinVCCCGEEEIIISQJ oEAnhBBCCCGEEEJs0+/bW+4U4tJCd30BKNYJIYQQQgghhJAkgAKdEEIIIYQQQghJArasmHd19XN2 DMTft3bu3mlBx/6TEj0mIvKGj2ydnzvQ0z58Pl+m35+K16zMDPnqS//5ffCP9Kys9LTUtDZ+f0Za mzR/hj/Vl5ae5WsjUn2ejuoXxozOyx0VHMrQMSNG50XZLrjZoEFRPpc/xpda+lpumTx5csj79u3b i5tuusnzfjdu3CiGDBkiFi1aJNq2bet5f+eee66488475ZJMpKWlJXoIScE111wjioqKxNdffy32 7dsnUlJSRNOmTUXVqlU967OwsFDk5eWJPXv2uNJeixYtxD/+8Q/59w8//CDPOSeUlJSEvD927Jij 9gghhBBC7PKrQBAnDTz33HNixIgRpe9nz54t7r//fscDs8OWLVvErl275EPn3r17xaFDh+SDlrFg /cGDB8WZM2eitlO/fn3RpEkTufTq1Uv89re/jbjt4cOHRb169ULW4SH0kksuceU3JStXXnml2LFj h/wbou/DDz90pd3HHnssRMiijyuuuMKVtg2+//57sX//fnH8+HFRrVo10bhxY1G5cmXttrVr1y59 WE9PTxcff/yxrT7XrFkjOnToELJu1apV4sYbb7TVnh0OHDgg6tSp41jMkKRhyPHmdzGBqsu89dZb olu3bqXvMzMzxUcffZTAERFCCCGkolLJaQOdOnUKeb9z506nTdqmdevWcikLiJZKlSqJunXrOu4T baSmpordu3eXrsOEwNku1tetWyfmz58v1q5dKzp27Ohauzk5OSFifcGCBeLRRx91rX0AYX7ppZfG tG2tWrVKxbpqcbPCxIkTQ95DuMdTqIMGDRrEtT9CygvGxKNBWRO6hBBCCCFe4TiW/eqrrxb33HOP OO+88+R7iNNkB0LFDXFuMHXqVCn4DY4cOeJa28kK9t+DDz4oXnvtNZGbm+tau3DFbd68een7uXPn uta2HRo2bFj6d5UqVWy1AUv66tWrQ9apgp2QCsfCTbUyk9AXYNu2bSHva9asmaCREEIIIaSi40ri OQi27777ThQXF4vp06e70WS54q677pKTFCtXrhQzZswQnTt3TvSQyjUDBgwo/Xvr1q0JdTs1TxzY fWifMGFCyPvs7Gxxww03OBoXIcQdTp48KZYtWxayDuFPhBBCCCEJoaggZ7Rr6eER9Apz6AUXXOBW k+UKBDIjG9jw4cMTPZRyz+DBg2UgtQF86lesWJGQscyaNUuMHz9eBrH37m3d8Pfuu++K999/P2Td yJEj3RoeIcQhyK6IhCZmWrVqFeUbQ6/LHJaEvgCEEEIIOetwnE2OEC944oknQnzEEV/Qt29fMWXK FHHxxRcnbmAWue6662QwvwGSGSCJwznnnJPAURFCjh49KoYNGybmzZsX9lm8Mz0SQgghhBiw2DpJ SvLz80OyEyKj06uvviqTAZQX3nnnnRBxDiAIKM4JSTw9evTQinN4zpzN4vzMjw8fpy8AIYQQUj6g WCdJCVKyo9i3uUYSUDM9JTNqxrjq1auLgQMHJmYwhJAQ1Ik0A3OtUUIIIYSQeEOBTpKWqlWrioUL F0oXdxQ5B3AXLw8gK9X69etD1iEzXkXN3UBIsqGLP09PTxejRo1KwGhIbHz1duN/0BeAEEJIxYGx 6aRc8O2338p0+n6/v1wUpv/ss89Es2bNSt+npKTIAs2XX355AkdFCDF4/fXXZb4LA7jCz5w5s1zl viCEEELI2UelsjchJPHUqFFD9OzZM9HDiJlTp06FvIfbPsU5IcnD3XffLXNewFsH1Rx++9vfJnpI 5CznwmcLJtIXgBBCiBVoTSfEA06cOCELMJeUlMj3q1evZsF0QgghhBBCSFQo0AnxiE8++UTs2bNH Zo5u06ZNoodDCCGE2GRt9ugB9AUghJC4U1SQM5qKnRBCCCGEEEIISQKY7p0QQgghhJyN+H869CF9 AQgh5RaKdUIIIYQQQgghJAmgQCeEEEIIISTZ+KDGtU3pC0BIhYZinRBCCCGEEEIISQIo0AkhhBBC znbyho9snZ97v6d9+Hy+TL8/Fa9ZmRny1Zf+8/vgH+lZWelpqWlt/P6MtDZp/gx/qi8tPcuXLlJ9 no7qF8aMzssdFRzK0DEjRudF2S642aBBUT6XP8aXWvpKiBDbqhan0fGhvFAp1g1//PFHMXjwYHHm zBkvxxPC3r17LW1fr149j0ZSNps2bQp5X61aNZGeni7+/Oc/iwULFsj9lpKSIi677DJx3nnnidOn T8sF642/ze+/++67kPby8/Pla5UqVcTUqVPFww8/HDYG3bFBn2YuuOAC8eabb4oJEyaI4uJi8dNP P4Vtj/HhFZ+hTbyq2+moVCm206l27dqiZcuWYuvWrWGfYX2DBg1iaicaJ0+eFOPGjQtbj+OycOFC 0blz55jaOXLkSNj3Y2XgwIFizpw5pe+nTZsmevbsWeb3MO7jx4+XvsexmDlzZsz9msG5ZKZOnTq2 2onE0aNHxSuvvBK2HufQq6++KmrUqFG6Dtvh+B47dixkWxyPr776Slx00UWujk1l48aN2vXBpxfX +yrrWsBx6Nq1q7xH4FrfvXu3WLRokTh06FDYtlOmTBF33XWX62M0qFy5srjzzjvl3zk5OWGf4xx+ 7LHHHPWhXkegXbt2ltq46qqr5FiysrIcjUXHgQMHxPz58yN+Xr16ddf7JIQQQgjREoiRoFhGETRP lqAACdSsWTOQmpoaqFWrVum6efPmRR2T2k5JSUmsP8dVgg/VYWMJPnzKz4IPvJ7sr507d4aNIyh4 Le2T4EOzbGffvn3y77L2X1CsB4KiIqT9Xr16BQoLCwPBh1tL++yNN96Qv0Mdb1DYyP3plBkzZmj3 W1AMWmonKDJD2hg7dqyl72dmZoZ8f/Xq1VG3D4rIsP3Sv39/S32a6dGjR0hbVo9TWUybNk17jo4b N067fVCka7cPilBXx6UD+1F3vnlx3wgKb+3vzM7Oluf+6dOnw75z8ODBQMuWLbXf27Fjh+tj1NG9 e3dt/5s2bXLUbocOHWzf74LiODBhwoTAqVOnXPqV4UQ6L5s1axYYNWqUvEcSQgghJPE8tmLvUMMX INFjiQcxW9OtWtFh2W7SpIlo2LChqF+/vnzFAiuSbjnnnHNKv3v48GFpfbniiiss9Vm1alVL27tF UPCGrWvbtq18Va3ibgDL9vLly8VDDz0Ush4WTBVYLiPtF1i1scQKjlHjxo1D1uF36iz7ZQHrIM4H WFxr1aolXnrpJbmvcJ4tWbJE3HfffZbbNDN79uywdbBS33777ZbaUS2/un0cjaC4F717/3+/Ingx rFmzJuL28Fgxey7UrFlTek/YRbWmwxvDTYLCM2wdjid+t47c3FwxadIkaT02s3LlSvF///d/ro5N RfV4AU2bNnX9vgHPo23btoWtHzBggHj55Zcjfu/CCy+UXhNBYRv2GTwBrN4P7YDzE1Z9lXXr1om0 tDTb7eqs6bEwbNgwOSbsGy/ZvHlzyHt4Q9xzzz3yPmL+v4kQQgghxGtiFuiXXnqpFGPr16+PuM3c uXNFq1atRGpqaoibq1Xq1q0rl/JCNIGOyQkv2L9/f9g6XV8QmG66EUNUm9G5rMfKDTfcIBewevXq UgG1bNkyRwL9k08+ka78Zm655Rbx5JNPWm7L7HYOMOlkhTvuuCPEtf/9998Xf//737UTBS+++GKY S/b48eMduf+fOnUq5L2bAh0uwqqwARA2CKuIBCYsCgoKQtZt377dtXHp+OGHH7R9eOHqjvuBut+B 3+8v87twAYdrtTqxd/DgQdfGF402bdrISQv1nqZeT1axK9A7derkuTgH6rnRo0cP8ac//cnzfgkh hBBSkUi9v1Uva3kBLKVmg8UL1h48jDdv3jy0oZQU0adPH3HNNdc4EurlEZ1Yx6QFgNhq1qyZq/0h Prpbt25h6yGQYH0140RM61BjZ5cuXSqFkFMwwWMQbUIoFtauXRvyHhZwWOvtoIp1YxLGCogtNgML 4TfffBOyDh4kaiw9zpuRI0da7s+Mem66Kdbh0aHLWdC3b9+o39NNeNgVc7GyY8eOMM8C4IVYjzTx gDj0soDl1nwtGHi9f8y0b98+bJ3VPCEquph7M5gENHudGCC/A/IWeA3ODzOIgyeEEEIISQQxW9PB +eefL4YOHSqXTz/9VFoJSxuqVKnCugXu27cv5D0EIZLEgcsvv1z85z//EV9++aW0lJaUlIg9e/ZI sYB9hm3xqi5w+4a4N1vN8X7UqFFRXdQhICGcDDZs2FCaGMopn3/+uXRPN4MHb7jCGlZxu5hFCVyh nSQTUy28SIh1ySWX2GoLx8uMVXd3cNttt4mOHTuKVatWyfcQO3Brf/3110u3gXu4KsKmT58uzj33 XBujjoybAl0nRGEJzszMjPo9NYQAxJp40C4693PghUBXzxmACUxj0q4sdCEyds47u+gmFJ1MECCR o+pdADGOiRqcL/AgwPWB/z8eeeQRUVhYWLod7i+Y8MHksJf/v6jnpNuTqoQQQgghMVNUkDPa9qOx mjrcvdTvI5qd7FR+awSoT7PwH1WfLi+++GK5WGHevHkhih2qpqyAcjz5mhU7UrsjwNnp0+6JEydE 9+7dtWoCfutuKnYA1W1Xsau+ur169bI7LK36ssMLL7wg1aGhXBDYDWULhfLRRx+FpIUHN998s/jN b37juF/1mnVTsWPmSQWqtKxzTaeeGzVq5Nq4dERyLYlVRVtBd1+MtWQC0ufr9qvbafqjoZtR0fnz x4ruGsrOzpbnvgriInA/QZyIAWJjkNTgiSeesD2GslCPDU3qhBBCCEkUrpUjj+Xh82xFFehuPdwZ ZnkDXTCwCuIOzKIMD/sQ+k747LPPpKk+kshR/eztoPpB6+IIYkX1r43F1zgSToSJmSuvvFK6RJjJ y8uTZvUhQ4aEXD+YiIE53Q1Uga5mAHSCGg8A1AQGOmAeVfHCtG1G9WkGSOjgRQ24SJMgsfiNo3aj 7l6q3gu8RBcM72RiR3cNRWoPkzuoi6aep5MnT5aJHbxCnVSJ54QIIYQQQogZ2wJdffAHSG1cETEL 9DFFr7c1+wK49WCtWphjyeiErH/InGYGaaZhibJzrF577TWZBSuSUIdfri5Y3irqb3Ui1s0Wf0wk YJ/YRbUEWimerpKfnx8S/AtRBt9eNQ05gnJbtGhhux8z3nnA2Juge/fdd7XByvAe8JJoSSTcJlLG wV27dpX5XbPvtwHS58NLJl7oxLqTCTkrYh0gexwEu9nnH+caEqMgU6QXqNcFi6UTQgghJFHYFuu6 gEm3LI/lDdWaHotFMRZUoa9L8a4DrqFm8PA5ceJEKbQ/+OCDmNp45513ZOrnfv36aa2mBhDWTtKR G6j7TA36t4L5PETogRNUge7kwR2WQng2RCsBACGkHj8nqAJdl0XNLjqLo5q9TyWSZ4c6qeQ2OnFs TrDhJpHOObMLt47f//732okwhGu4naggGrrEA068MHT/L5Q10ZWVlSWzlZrBxBtCbrzIKKcKdCcT cYQQQgghTrAt0HUP57EKSLdQxxCPVMA6VAHrlUCPdQIEwhruoSpwl0e2pltvvVVaxpHZDqnGkV78 n//8pygqarSm9THDF6BIDB8+XLoDQzzpik2ruFUzCoLfnFFMFx8bK2bLn5N2gCrWnYpd5CeAe3Mk ayJSvrtZi0oV625OqOmsxjgfcF7pQNw1frsKzk+reRusgH512dC8EuuoK6kLf0GeiEjg2lRDIwCu CXhhOOHxxx+XhdexoP5fNFBvTzex4SScx6o13eCBBx4QgwYNClmH8AEIdmSo8xKKdUIIIYQkCtti HbW/VIu6EwuoHdSEU7r403igiji3xHq9evVC3sPl8/vvv4/pu7/73e/EK6+8ok2jjeLksJLjoRuu tOgHicwQ1w4LlpVJFwjgb7/9Nubto2H+vdEs+GVhnuRwck4uXrw4zLIIjwRMbjjhuuuukwn9VCB4 ndZfU1GvUTet6ZGKgcMbQFejD278ugmT/v37uzYmHbpkbMArgQ5QfFsFwjc3N1dOGBighAKSqGEf 6MIHsB7C2i4oAI7jAXd/LCgzgHIdke4js2bN0o6jQ4cOtsdgV6AD3I/UGogom4EQHjdR75MVOdcK IYQQQhKLo+RxqjU73gJddcFMhEDHg64qeqK5M1tBlxXZyoMjxAASdekKMLtJJAFkFfOEix3L9/wN 532m1ggw1waDUIjV3R8gfr+oqEi0bt1aWu3UOGpY8xYtWmR5nCq6bOcQVZUrV3bcthk1pthNa3rX rl2159mSJUukMDcEOyyfDz/8sNaSjski1M7zkkgJ3Jo3b+5Zn4ij1uXyQEZ/7LPbb79desBgYgnx 6LprHPc6ZD53AioKqKDqAKzU8Koxs2LFCu0kEsabkZFhewy6CaJYxTpc/nHeqBOz+F3PPPOM7TGV NZ6KGsZFCCGEkMTjSKyrorQiWtN1pcnccpXUiXWrRaZRIg3xriNGjNAKBivA2o3i6aroc0usm70Q nBRrVpPZoeB8WV4IEJOwPEK0wasgWqI+XfIzK0AYqTHayHR+3333OWpXBwSwGSdeCioQT8h5oMM4 TxBjDIE3Y8YM7XY4L2vUqOHamHToBDo8F7zsF8n/InkJ4BhgkidaOAmuc+xDeC05IVIiO7QNb5pn n31WvPXWW+Lee++VIS46YerUcq3L52AlxwPCb9RkcgChIahC4QbqxLPuvk4IIYQQEg8cKTY1SdLu 3budNGcZ1ZruJCO4XbwU6Lq27SSROv/88+WDOKy2cHe1Oj5sD5GLCRA8yHt13M0C3Ukc+Y033hji 8r5hwwYZ8wwLodkNG3+/99570t0Y20OIlDXJA0ubzpXZCrNnzw47tlOnFi3ucdLwBQi3YrqBKkKc TjSoYIIhkls0hB+OQ6T8Bdj/TuOuY0E3ieil27sBckXYrQePyQ2c004ZNmxYRGGMEBeEWmBya+7c uVqLPiZ7MKHiBHXCCFi9H1177bVhieVwfuHe5gbqpEa8J54JIYQQQkopKsgZ7Uixq0+68VbMqnJc v369eOqpp2RBapiJ1qxZI7Zs2VJmADV8cmGagXpDJiekXX7++efFiRMnyhyDTlU7KTRsRjWpOzWJ o4D3H//4R2lifOmll0Tv3r0jFgnGUzRqQEEtYPunn35a1K5dW36mzpTEUhQ6Fsz+00i/7CQ74LRp 00LeI6gVNb/wu5ChDRnrjN8In+NYfgMU18KFCx0FDMOnXlUb2dnZokuXLrbbjIZ6rNxW6QAzEDol Fg1cI/Bbrlq1quvjUdGpz3iodJiCkcHRSmF4XI/INPfQQw+5MgbEbuC+aLfsAa4jp2Z9XQ1AO2UT kFFOVeWrVq2S922nqBny3HITIoQQQgixijUHagU1qDOWgsBuovYPs5CbZjn488K8FE08xVOgW/V3 jwSENh52sQBMTsDUCbMUxg7TNsQy6ofpUH3e3UrzrwY4wwUAIscOd9xxhzSRI4ueGYgFuyLVDSGN AFvVBSGS37gbpKenh7z3QKDv73D3k6V5AS6//HKxevVqGdAfi8jBOQ3/fydBz1bQZb2Lh1gHmBjC vsHxxiRNpOL1uL5w7iLlO9LFuwl88eHagLiO5cuXx/y9IUOGlN4vnKCr42nXBQmTh4jnMdcAhOuC U/eDVq1ahbynWCeEEEJIonDVmp4Ise6WMNYBYTNlypSo2+jEulsWQtUK6JZYV4F1GCnIb7rpJvkK wRVJqAM1MYFbYl21+OmyrFkBHgNIa28XJzWoIqFmBINffufOnV3vx0AVp15Y0wGstjheEyZMiFju AN4g8GhAYHbPnj09GYcOZLozF2eHh4GaQtxLYI1GtjOUDoAAx6QPBCE8OeCTDq8CXEPYxm1xboAJ uqVLl8oshTrBbAaTBbjvwaPIDXC/UD2B7FjTgZFRzuwlggkQpM13gjqpFe9YLkIIIYSQUgIOOHPm TCD4MBdAM8ayZ88eJ01aJvjAH9K/20tQFMvfGYklS5aEbe8Wx48fDzRq1Ki07ZYtW7rWthMKCwtD fnNQ7LjS7qlTpwJB8VDablBcu9LuK6+8EqhTp07Mxzz4sB4Iiib5XfN4evTo4WgcK1euDOsL67wm KJhL++vfv7/n/Z0+fTrw5ptvBsaNGxcYMWJEICjaA3PmzAns27fP876jsWnTJrm/cZ6VUu+9ynUM X4DEDS1hFBcXB3JycuR9y3wP8/v9genTpweOHDniep/t27d39X65devWQLt27QLVqlULpKSkBJYu XeqovY0bN4Zco717V8QzgxBCCCHJgCPzLCyuyB5lrk+F+PRLLrnESbOWGDt2rLQOwf3RSQaySMCi DQskYpl1qJZDuLMi1t0NizrSUcNCCSsY0o/H0wIYDVgDvQC1yGD9XbdunXyPuFM3QI26Xr16yTpU sFxin5rdjuGlAOsmssShNhhi+M2fGfWkvDi/CCGEEFKB+X9MRGXEAHgFAA==
Good luck!
Explore CTF challenges online
If you’re eager to dive into the world of Capture the Flag (CTF) competitions and enhance your team’s cybersecurity skills, numerous platforms offer a wide range of challenges. Here are some reputable websites where you can find CTFs to test your team’s abilities:
- Hack The Box (HTB):
- Hack The Box provides a platform for practicing penetration testing skills. It offers a variety of challenges in different categories, allowing users to learn and improve at their own pace.
- OverTheWire:
- OverTheWire hosts various online war games aimed at helping participants learn and practice security concepts. The challenges range from beginner to advanced levels.
- CTFtime:
- CTFtime is a central hub for information on upcoming CTF events, team rankings, and write-ups. Explore the platform to discover ongoing and upcoming competitions from around the world.
- Root Me:
- Root Me is a platform that offers a variety of challenges, including web exploitation, reverse engineering, and network analysis. It caters to both beginners and experienced security enthusiasts.
- PicoCTF:
- PicoCTF is an educational CTF platform designed for students and beginners. It covers a broad range of topics, making it an excellent starting point for those new to cybersecurity.
- VulnHub:
- VulnHub provides a collection of vulnerable virtual machines for users to download and exploit. It’s a great resource for honing practical penetration testing skills.
- CTFlearn:
- CTFlearn offers a platform for individuals to learn and practice cybersecurity skills through a variety of challenges. The platform is suitable for both beginners and advanced players.
- GitHub CTF Archive:
- The GitHub CTF Archive is a collection of CTF challenges and competition archives. It serves as a valuable resource for accessing challenges from past events.
Remember to approach these challenges with a positive and inquisitive mindset. Each CTF platform has its unique offerings, allowing you to explore different aspects of cybersecurity.
Games, cyber security, and better collaboration
Capture the Flag is more than just a game; it’s a valuable tool for developers to dive into the world of information security in a fun and collaborative way. Whether you participate in existing CTF competitions or create your own challenges, the experience gained can significantly contribute to your understanding of cybersecurity.
As you embark on CTF challenges, leveraging project management tools like Backlog can significantly enhance teamwork. Streamlining communication, organizing tasks, and tracking progress becomes seamless, empowering teams to collaborate effectively. Utilizing tools that align with the spirit of collaboration ensures that the lessons learned in CTF competitions extend to real-world projects, fostering a culture of continuous improvement and shared success.
So, why not give it a try? Start exploring the exciting realm of CTFs and make learning about security an enjoyable adventure for your team!
This post was originally published on May 3, 2019, and updated most recently on December 4, 2023.

